European NIS-2 Directive
The NIS-2 Directive, officially known as "The Network and Information Security (NIS) Directive," was published in the EU Official Journal on December 27, 2022, and came into effect on January 16, 2023. It governs the cybersecurity and information security of businesses and institutions. EU member states are required to transpose it into national law by October 2024.
The NIS-2 Directive enhances cybersecurity requirements and sanctions to harmonize and improve the security levels across member states. It imposes stricter requirements on various sectors, addressing topics such as cyber risk management, control and monitoring, incident response, and business continuity. Additionally, the directive broadens the scope to include more organizations. Stricter liability rules will apply to the management of affected organizations.
Do you have questions?
Sectors in Scope
Sectors with High Criticality
Other Critical Sectors
Is Your Company Affected?

Check whether your company
falls under
High Criticality or
Other Critical Sectors

If YES

THEN, depending on
| Size |
|
| Sector | |
| Criticality |

Your company falls either under
Essential or Important entity
Essential & Important entities
Sector |
Large Entity |
Medium Entity |
Small Entity |
Micro Entity |
|||||||
Transport |
Essential | Important | Not in scope | Not in scope | |||||||
Energy |
Essential | Important | Not in scope | Not in scope | |||||||
Digital Infrastructure |
Essential | Essential | Essential | Essential | |||||||
Employees OR Annual Turnover |
|||||||||||
| Large Entity | Medium Entity | Small Entity | Micro Entity | ||||||||
| >=250 | >€ 50M | 50-249 | 10-50M | <50 | <10M | <10 | <2M | ||||||||
Timeline
17. Dec 2022
NIS 2 Directive was published as Directive (EU) 2022/2555
17. Oct 2024
Member States must adopt and publish the measures necessary to comply with the NIS 2 Directive
17. April 2025
Member States shall establish a list of essential and important entities
17. Oct 2027
The Commission shall review the functioning of this Directive
Deadline for Entities
- 17th Oct 2024 deadline only concerns the transposition into national law
- It does not mark the point in time from which the requirements are valid for affected companies.
- There will be a reasonable implementation period for affected companies to comply with the national law
Supervision
Measures |
Essential Entities |
Important Entities |
||
| Inspection | On-site inspection and off-site supervision, incl. random checks conducted by trained professionals on | On-site inspection and off-site ex post supervision | ||
| Audit | Regular and targeted security audits carried out by an independent body or a competent authority; incl. Ad hoc audits. | Targeted Security Audits | ||
|
Security |
Security scans based on objective, non-discriminatory, fair and transparent risk assessment criteria | |||
|
Information Requests |
Requests to access data, documents and information necessary to carry out their supervisory task. | |||
| Further information requests | Requests for information necessary to assess the cybersecurity risk-management measures adopted by the entity concerned. | Requests for information necessary to assess, ex post, the cybersecurity risk management measures adopted by the entity concerned. | ||
What happens if you do not comply with NIS?
Fines
- Firms that fail to adhere to NIS2 could face substantial penalties depending on their classification as essential or important entities.
- Essential entities: can be fined at least € 10M or 2 % of the total worldwide annual turnover in the preceding financial year.
- Important entities: can be fined at least € 7M or 1.4 % of the total worldwide annual
Legal consequences
- Non-compliance with NIS2 not only risks fines, but also legal consequences for management teams failing to meet the new requirements.
NIS 2 Main Areas of Requirements
NIS 2 Cybersecurity Risk-Management Compliance: A Dual-Security Approach
- Integrating IT and OT Security for NIS 2 Compliance:
- Organizations must merge Information Technology and Operational Technology security strategies. This integration is vital due to the expanded attack surface from IT and OT convergence, ensuring cyber threat protection and operational resilience.
- IEC 62443 Standards for OT Security:
- These standards provide a framework to secure Operational Technology systems, especially in critical infrastructures. Adherence to IEC 62443 enables proactive management of OT-specific risks, the establishment of robust security controls, and maintenance of operational integrity.
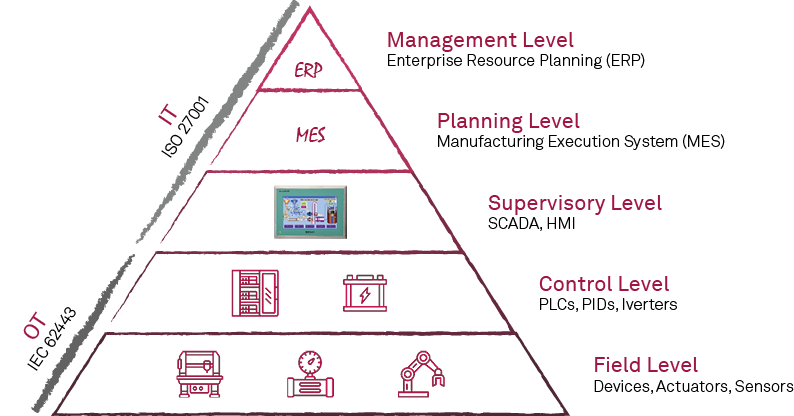
- ISO 27001 Framework for IT Security:
- This standard is crucial for systematic management of IT security risks. It outlines requirements for an Information Security Management System (ISMS), ensuring data protection, legal compliance, and a structured method for assessing, managing, and mitigating IT risks.
Cybersecurity risk-management measures
- Policies on risk analysis and information system security
- Establish processes for regular risk analysis and vulnerabiliy assessment.
- Conduct asset identification, documentation, and software cataloging.
- Identify and document current security weaknesses and vulnerabilities.
- Routinely execute penetration tests on internal infrastructure and existing security implementations.
- Adopt an Information Security Management System (ISMS) in line with standards like ISO 27001, TISAX, and others.
- Incident handling and management
- Business continuity and crisis management (back‐ups, disaster recovery)
- Supply chain security
- Security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess the effectiveness of cybersecurity risk-management measures
- Basic cyber hygiene practices and cybersecurity training;
- Policies and procedures regarding the use of cryptography and, where appropriate, encryption;
- Human resources security, access control policies and asset management;
- The use of multi-factor authentication or continuous authentication solutions, secured voice, video and text communications and secured emergency communication systems within the entity, where appropriate.
How can msg Plaut help you?
Compliance Strategy Development
We simplify the complexity of the NIS 2 Directive, offering you a clear, step-by-step compliance plan that fits your organization's timeline and processes.
Gap Analysis & Actionable points
Through our gap analysis, we pinpoint exactly where you stand with NIS 2 compliance and provide you with tailored solutions to address the issues
Compliance
Assistance
Count on our experts for help throughout the process of meeting NIS 2 requirements, from the first steps to full compliance.
Compliance
Training
Our training will give your team the knowledge they need to understand and implement the requirements of the NIS 2 Directive.




